Whether we do vulnerability assessment, web app code review, or mobile app security testing, we provide our customers with a comprehensive set of testing deliverables. We report the testing results and document our experts’ recommendations regarding feasible security enhancements.
Security Testing
Security testing helps identify vulnerabilities and potential threats in your software, ensuring it remains secure and resilient against cyberattacks. By proactively addressing security risks, companies can protect sensitive data, maintain user trust, and avoid costly breaches.
Our Security Testing Services
Vulnerability assessment
Penetration Testing
Static Code Analysis
Social Engineering
Pre-certification security audit
Compliance Testing
Our Penetration Testing Process
At Adroitics, we are dedicated to protecting your application and data from cyber threats. Our penetration testing services are crafted to uncover vulnerabilities, simulate real-world attacks, and enhance your security posture. Here's an overview of our penetration testing process:
Discovery & Scoping
Reconnaissance & Vulnerability Analysis
Exploitation & Attack Simulation
Post-Exploitation Analysis
Remediation & Retesting
DevSecOps
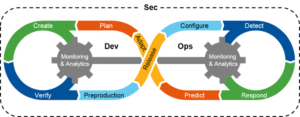
Our Deliverables
A detailed report describing performed testing activities
A list of revealed vulnerabilities classified by their type and severity
A set of hands-on enhancements for each detected loophole
A step-by-step action plan for software security optimization